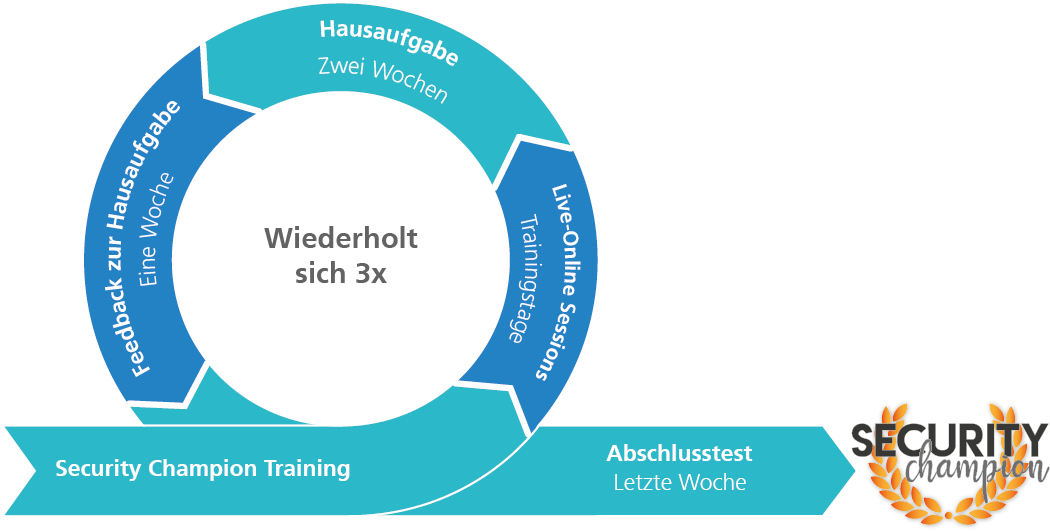
The requirements for secure software applications in companies are continuously increasing. Protecting data and safeguarding systems against external attacks is becoming increasingly important - and complex. In our security champion training course, we show your team of software developers how they can consistently take security into account in their daily work. In the future, the security of software applications can only be guaranteed by building up the skills of developers in a focused way.
By completing this training course, you will qualify as a security champion and become an expert in the field of secure software development. We provide you with the necessary knowledge and skills on a step by step basis so that you can advise your teams on security issues and point out possible gaps in security in your role as a security champion. In addition, you will practice the necessary hard and soft skills and learn how to successfully apply the latest security methods and the relevant tools. The learning content is based on the entire software development process and is coupled with extensive practical sessions.